- 07 May 2025
- 5 Minutes to read
- Print
- DarkLight
- PDF
SSH Tunneling
- Updated on 07 May 2025
- 5 Minutes to read
- Print
- DarkLight
- PDF
This feature is only available for the Enterprise plan.
👤 This documentation is intended for Workspace Admins. Check with your Team Admin for additional access.
Overview
Preset can connect to some databases securely by first establishing a connection to a server in between Preset and your data warehouse. Using this SSH Tunnel, communication between the data warehouse and Preset will be encrypted even across insecure networks.
When to use SSH tunneling
In general, there are two basic use cases for an SSH tunnel:
- When a direct connection is impossible.
- When a direct connection is forbidden due to a security policy.
Sometimes when a data warehouse is inside an enterprise environment, direct connections are blocked by security devices such as firewalls and intrusion prevention systems. Bastion hosts can first connect to a server on the edge of the protected network and then establish a second connection to the data warehouse within the internal network, patching these two connections together. Preset can automate this process using the SSH tunneling.
Another common case where direct connections are impossible is when connecting to a data warehouse that is only accessible locally and does not allow remote connections. In this case you will be opening an SSH connection to the data warehouse.
Before you start
Before starting, allowlist the following IPs to ensure that Preset is whitelisted in your firewall:
| us-west-2 (us1a) | us-east-1 (us2a) | eu-north-1 (eu5a) | ap-northeast-1 (ap1a) |
|---|---|---|---|
| 35.161.45.11 | 44.193.153.196 | 13.48.95.3 | 35.74.159.67 |
| 54.244.23.85 | 52.70.123.52 | 13.51.212.165 | 35.75.171.157 |
| 52.32.136.34 | 54.83.88.93 | 16.170.49.24 | 52.193.196.211 |
If you are not sure where your Preset workspace is located, you can refer to the URL on your browser when accessing Preset. It should look like this: https://xxxxxxxx.us2a.app.preset.io/superset..., where us2a means it is in us-east-1.
How to use SSH tunneling
To use Preset's SSH feature, follow the main instructions for connecting your data. Enter the Primary Credentials portion of the connection form as if connecting to a publicly addressable database.
Specifically:
- In the Host field, enter the hostname for the data warehouse as it is seen from inside the network.
- In the Port field, enter the data warehouse port as seen from inside the network.
Scroll down to the SSH Tunnel and toggle it on.
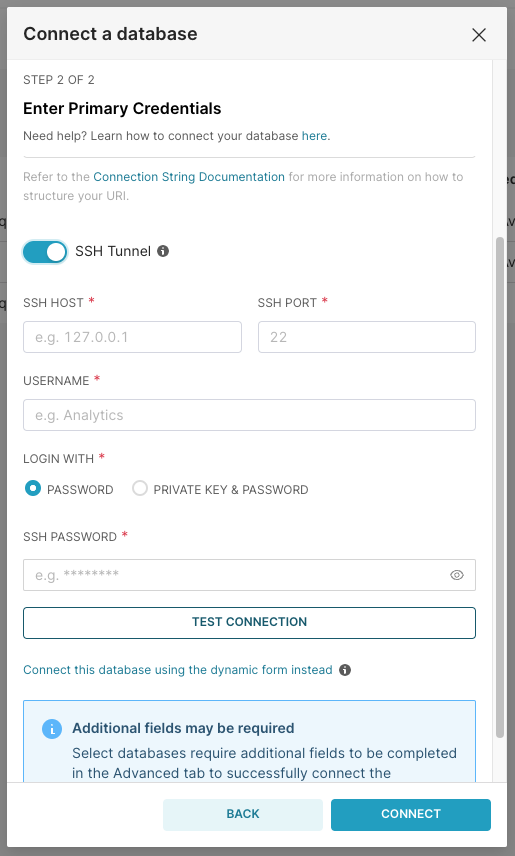
In the form that shows up, enter the following details:
- In the SSH Host field, enter the external name of the SSH bastion host as seen from the outside of the network (or wherever you are).
- In the SSH Port field, enter the SSH port as seen from outside the network. This is usually 22, regardless of which data warehouse you are connecting to.
- In the SS Username and SSH Password fields, enter the username and password you use to login to the bastion host.
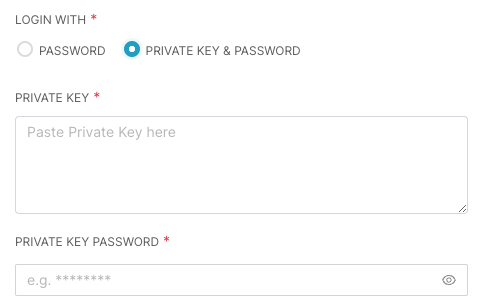
If you're using an SSH Private Key, you can choose Private Key & Password to pull up the Private Key & Private Key Password fields.
Only RSA keys are supported. Other key types (such as ED25519 are not supported).
When done, select Test Connection to see if it works — a notification message will appear. If no additional connection settings are required, then go ahead and select Connect.
Troubleshooting the SSH connection
Case 1: Not stablishing any SSH Connection
If you have problems connecting, verify the SSH host port and password by connecting manually using ssh or PuTTY on older windows systems.
If you’re unable to test the SSH connection, you can try to connect to the SSH server/Bastion Host using ssh directly:
ssh <SSH tunnel username>@<SSH tunnel host> -p <SSH tunnel port>
Case 2: Flaky SSH Connection
There are times when you set up the SSH connection correctly, nevertheless, when you load a dashboard you created, some charts inside it are giving an error saying Can’t establish connection to SSH gateway.
This issue commonly appears because the environment where you database lives (e.g. EC2) is cofigured to accept a certain maximum number of concurrent SHH connections and your dashboard (or report) asks for more connections than the limited stablished there. To overcome this situation, you can investigate the amount of SSH sessions opened in your dashboard/report, and compare that number with the MaxSessions variable in your environment.
The default MaxSessions variable commonly is set to 10 in EC2 environments, if your dashboard asks for more sessions than that, then you will see flaky SSH connections in your report/dashbord. The MaxStartups variable is also commonly set to 10 by default, which could block the SHH connections if your dashboard asks for more requests than that.
If you increase those variablesin a way that suites your request requirements, you will help your dashboard/report to display the charts correctly (e.g. increasing MaxSessions allowed to 30 and MaxStartups to 30:60:100)
Running SSH directly
Preset's SSH tunneling feature conveniently wraps around SSH and automates the common cases of connecting through a tunnel. Preset uses a built-in SSH client that doesn’t depend on the installed system’s SSH client. This allows connections from systems where you can’t run SSH manually or do not have shell access. Consequently, Preset can’t take advantage of authentication services provided by the system, such as Windows Domain Authentication or Kerberos Authentication.
If you need to connect using a method not enabled by Preset, you can often accomplish this by running SSH directly:
ssh -Nf -L input-port:internal-server-name:port-on-server username@bastion-host.domain.com
This allows you to use the full array of features included in SSH. If you find yourself doing this often, please let us know so we can make improvements.
Disadvantages of indirect connections
While using an SSH tunnel makes it possible to connect to a data warehouse that is otherwise inaccessible, it’s almost always preferable to use a direct connection when possible. Several limitations include:
- If the enclosing SSH connection is closed because you put your server/computer to sleep or change networks, all established connections will be closed as well. This can cause delays resuming connections after suspending your server/computer.
- SSH will be slower than a direct connection. The connection has to go through an additional host that mediates the connection to your database.
- Multiple operations over the same SSH tunnel can block each other and increase latency.
- The number of connections through a bastion host is often limited by organizational policy. Some organizations have IT security policies forbidding using SSH tunnels to bypass security perimeters.
That's it! You should now be able to connect to your database via SSH.
