- 16 Nov 2022
- 2 Minutes to read
- Print
- DarkLight
- PDF
SAML Single Sign On (SSO) Integration
- Updated on 16 Nov 2022
- 2 Minutes to read
- Print
- DarkLight
- PDF
The SAML SSO integration is only available on the Enterprise plan.
Overview
Preset supports implementing a Security Assertion Markup Language (SAML) Single Sign On (SSO) integration, enabling companies to leverage their existing identity management system, and allowing employees to sign in to Preset using their Identity Provider account.
Instructions for this implementation are detailed below.
Supported Identity Providers
The steps to create the integration vary according to the Identity Provider (IdP) used, however, any IdP that supports the SAML SSO protocol should be compatible.
We have official tutorials for below IdPs:
If your IdP doesn't have an official tutorial, follow below instructions:
General guidelines for the SAML SSO integration
- Create a SAML application in your IdP and include the following SAML attributes:
email
firstName
lastName
sessionDurationSecs
Note: The sessionDurationSecs attribute is optional, and can be used to control sessions timeout (in seconds). Default value is 86400 (24 hours) - Max value is 604800 (number of seconds in 7 days).
If your IdP requires a Single Sign On URL and an Audience Restriction URN (SP Entity ID) to create an application, use below placeholder values:
- Single Sign On URL:
https://auth.app.preset.io/login/callback?connection=auth0_connection_name - Audience Restriction URN (SP Entity ID):
urn:auth0:preset-io-prod:auth0_connection_name
- Send the following information to us by opening up a support ticket via the Preset Support Portal:
- SSO Login URL
- X509 Signing Certificate
- Sign-out URL (optional)
- Your company domain (for the SSO enforcement).
The SSO integration will be enforced to all accounts from your domain(s). This means that all users from your domain(s) that use Preset need to be properly configured and assigned to the Preset application in your IdP.
To mitigate impact, the integration needs to be approved by an admin of your Preset team. If you are not a Team Admin, share the support ticket with one so they can approve the implementation.
Preset will return registration information (permanent values for the Single Sign on URL and the Audience Restriction). Update your SAML settings with this additional information.
After updating the configuration, test the integration.
Important details
Existing accounts
If users have already been created in a team before setting up the SSO integration, Preset will merge existing users with the SSO login. For a successful merge, the email sent by the Identity Provider needs to be the same used on Preset side.
New accounts
Preset supports just-in-time account creation (JIT Provisioning), meaning that a Preset account is automatically created for a new user authenticating via SSO. However, this account will not be automatically added to an existing Preset team. Instead, a new Team will be created. Make sure to invite new users to your Preset team to prevent this issue.
Testing the integration
Navigate to the Preset log in page.

Enter your email address and click on Next.
You will be redirected to your IdP to perform the authentication. Once the authentication is successfully finished, your IdP will send you back to Preset.
You'll be prompted to Link accounts - click on RE-AUTHENTICATE.
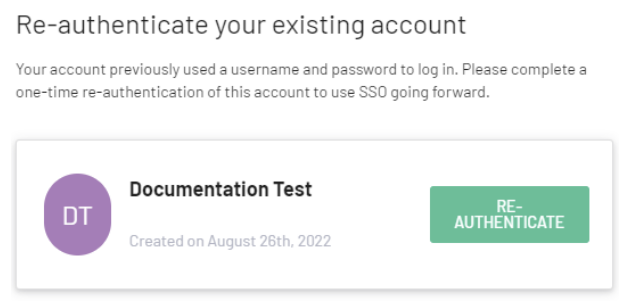
- Enter the local password set before the SSO integration, and click on Log in.
You should be logged into your existing account, with all existing permissions.
