- 06 Jan 2026
- 5 Minutes to read
- Print
- DarkLight
- PDF
Role-Based Access Control (RBAC)
- Updated on 06 Jan 2026
- 5 Minutes to read
- Print
- DarkLight
- PDF
Role-based Access Control Requirement
Role-based access control is only available for the Professional and Enterprise plans.
Workflow for RBAC
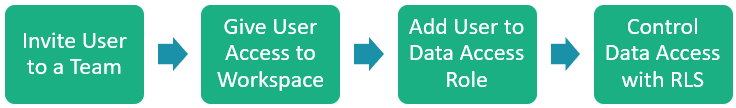
To set up Role Based Access Control, you'll follow this flow:
Invite a user to a team
Add them to a workspace
Add them to a data access role; and,
Control data access with row level security (RLS).
Role Details
The available workspace roles are as follows: Workspace Admin, Contributors (Primary, Secondary, Limited, and Visualization), Viewer, Dashboard Interactor, and Dashboard Viewer.
Workspace role definitions are as follows:
Feature | Workspace Admin | Primary Contributor | Secondary Contributor | Limited Contributor | Visualization Contributor | Viewer | Dashboard Interactor | Dashboard Viewer |
|---|---|---|---|---|---|---|---|---|
Dashboards | Read, Write Access, Embed Access | Read, Write* Access | Restricted Read*, Write* Access | Restricted Read*, Write* Access | Restricted Read*, Write* Access | Restricted Read* Access | Restricted Read* Access | Restricted Read* Access |
Charts | Read, Write Access | Read, Write* Access | Restricted Read*, Write* Access | Restricted Read*, Write* Access | Restricted Read*, Write* Access | Restricted Read* Access | No | No |
Drill to Detail | Yes | Yes | Yes | Yes | Yes | Yes | No | No |
Drill by | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No |
Database Connections | Read, Write Access | Read Access | Read Access | Restricted Read Access | No | No | No | No |
Datasets | Read, Write Access | Read, Write Access | Restricted Read*, Write* Access | Restricted Read Access | Restricted Read Access | No | No | No |
SQL Lab | Read, Write Access | Read, Write Access | Restricted Read*, Write* Access | Restricted Read*, Write* Access | No | No | No | No |
Alerts and Reports | Read, Write Access | Read, Write Access | Read, Write Access | No | No | No | No | No |
Annotation Layers | Read, Write Access | Read, Write Access | No | No | No | No | No | No |
CSS Templates | Read, Write Access | Read, Write Access | No | No | No | No | No | No |
Data Access Management | Read, Write Access | No | No | No | No | No | No | No |
* Restricted read access is controlled by the data access roles. Restricted write access is controlled by data access roles when the user is creating the content from scratch, and it is controlled by content ownership when the user is editing the content.
Data restriction (via data access roles) is possible for the following workspace roles:
Secondary Contributor
Secondary Contributors have access to all data within a workspace, but are subject to data restrictions as defined by a data access role. This role grants restricted dataset write access to the users. For example, they can create physical datasets from databases or schemas they have access to, they can edit datasets if they are the owner, they can create and manage alerts/reports, and they can upload CSVs if CSV upload is enabled in the database they have access to. They can also export and import assets.
Limited Contributor
Similar to the Secondary Contributor, this user role has access to all data within a workspace, but is subject to data restrictions as defined by a data access role. Limited Contributors can't create physical datasets from databases and schemas, and they can't upload CSVs to databases. However, they can create virtual datasets and charts/dashboards using the data they have access to. They can also export and import assets.
Visualization Contributor
Similar to the Limited Contributor, this role has access to all data within a workspace, subject to data access role restrictions. However, Visualization Contributors are further limited to focus exclusively on creating charts and dashboards without technical data access:
No access to SQL Lab or the ability to view/save SQL queries
Cannot create datasets
No access to the Database Connections menu
This role is designed for business users who need to build visualizations using pre-configured datasets without requiring SQL knowledge or access to underlying data sources. They can also export and import assets.
Viewer
This user role only has access to visualizations (charts and dashboards) that are published, and is also subject to any defined data access role-based restrictions. For example, an external marketing agency may be given view access to published visualizations from a specified dataset. They can export assets, but not import.
Dashboard Interactor
This user role only has access to dashboards that are published, and is also subject to any defined data access role-based restrictions. They can view or interact with dashboards by drilling to chart details. For example, a regional sales manager needs to view a sales performance dashboard and interact with the data filters and drill-down capabilities to investigate specific sales trends in their region. They can only export dashboards, but not import.
Dashboard Viewer
This user role only has access to dashboards that are published, and is also subject to any defined data access role-based restrictions. For example, a potential business partner is given view access rights to a quarterly product sales dashboard used in a presentation by your company. They can only export dashboards, but not import.
All of the roles above are assigned to specific users in Preset Manager on the Workspace Roles screen (see Invite Others to your Team to learn more).
Change User Access to a Workspace
Each user's workspace role is set when their invite is sent but can be updated later as needed.
To edit a user's workspace role, select the vertical ellipsis icon in a workspace card and, in the sub-menu, select Edit Workspace Roles.
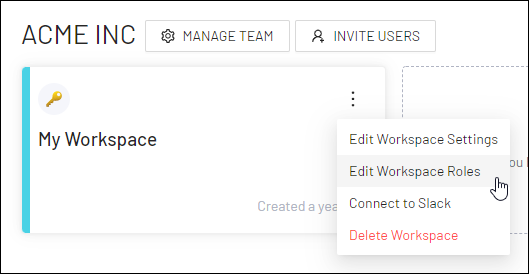
The Workspace Roles screen appears.
Under the Workspace Role column header, modify a user's workspace role as needed (see Role Details to learn more).
.png)
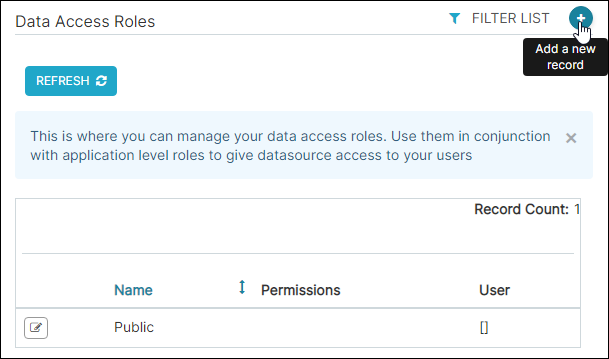
Navigate to Data Access Roles
In the Toolbar, hover your cursor over Settings and then select Data Access Roles.
The Data Access Roles screen appears.
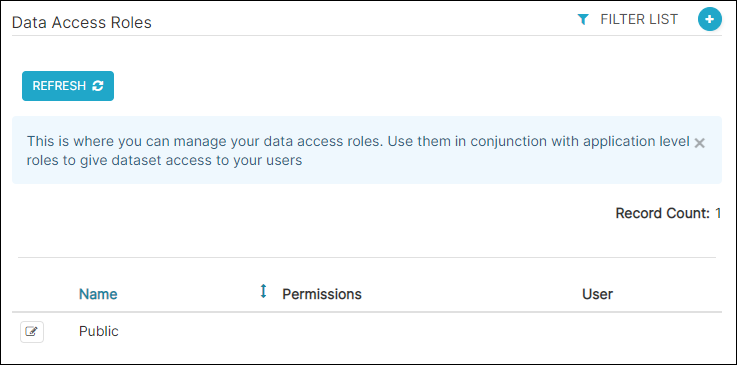
Add a Data Access Role
Select the plus icon to add a new access record.
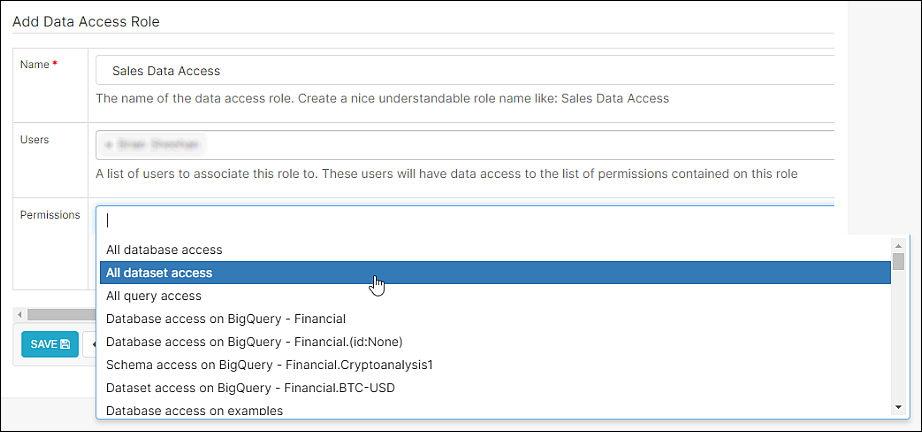
The Add Data Access Role screen appears.
In the Name field, enter a memorable name for the data access role.
In the Users field, select one or more users to assign to the data access role.
Lastly, in the Permissions field, select one or more data access permissions to associate with the role or leave this field blank if using Row Level Security to create more granular data access.
Types of Permissions
All database access
All dataset access
All query access
Database access on
Schema access on <database.schema>
Dataset access on <database.table>
When done, select Save.
Levels of Data Access Coverage
Wide Access
- All database access
- All dataset access
- All query access
Specific Datasources
For more granular data access, Workspace Admins can manage what users can use when creating charts or what users see when viewing dashboards and charts.
- Database Access: Databases defined on Sources / Databases, used for Secondary Contributors, Limited Contributors, Viewers, and Dashboard Viewers.
- Schema Access: Schemas available on the Databases defined on Source / Databases used for Secondary Contributors, Limited Contributors, Viewers, and Dashboard Viewers.
- Dataset Access: Dataset defined on Sources / Tables, used for Secondary Contributors, Limited Contributors, Viewers and Dashboard Viewers.
- At minimum, dataset access to one physical dataset is required for a users to be able to see the SQL Lab tab.
Data access roles are defined on the Edit Data Access Role screen (see Add a User to a Data Access Role to learn more).
Note that Workspace Admins are the only users that can create, modify, or delete a role.
Control Data Access with Row Level Security
Row Level Security (RLS) is a powerful feature that enables you to exert a granular level of control over who can query—and view—specific data in selected datasets. This level of query-based access control empowers organizations to align data access permissions (via roles) with larger-scale business initiatives.
You can find more information and a walkthrough on the Row Level Security (RLS) page.
